The advanced risks climate is extending as firms rely more upon IT and PC organizations to carry on with work, exposing business environments to new significant threats. Cyber threats jeopardize organizations by making negative disturbances in everyday business activities. Frameworks could neglect to work or delicate information gets into some unacceptable hands. Organizations can utilize cybersecurity weakness evaluations to more readily recognize, screen, and prevent a wide range of cyber threats. It’s a significant piece of your alarming management of the board structure and information security exercises.
What is a digital protection report?
A cyber security report contains fundamental insights about cybersecurity issues, weaknesses in the computerized climate, safety control shortcomings, and security program viability.
Cyber security reports help in the improvement of data-driven communications among sheets, directors, security and threat pioneers, and security experts. It guarantees that all partners are participating in further developing security systems and decreasing risk.
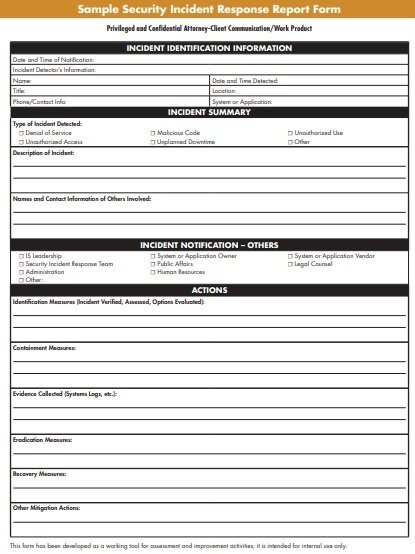
sample security incident response report form
security incident report template
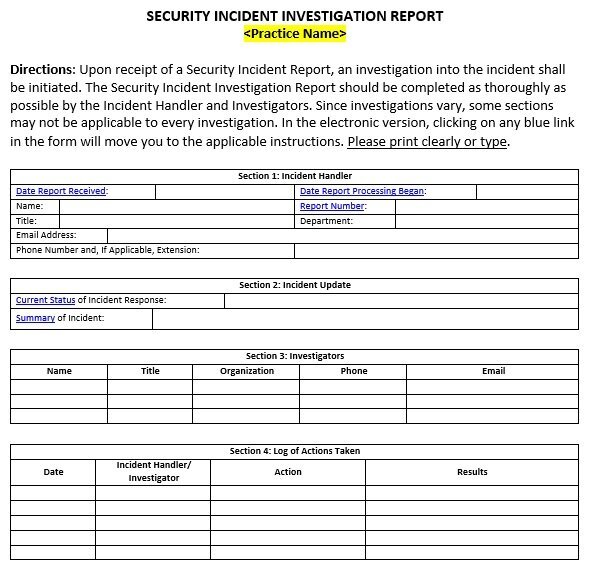
security incident investigation report template
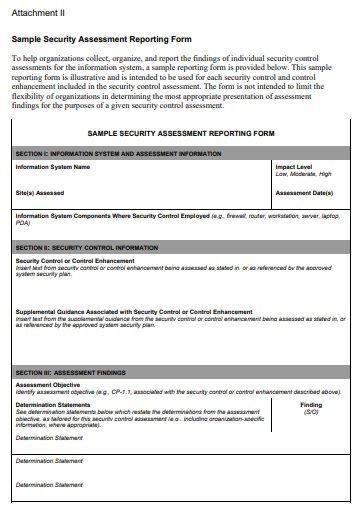
security assessment report template
annual security report template
free security report template
free security report template 1
annual campus security report
free security report template 2
facility related control systems security assessment report template
Significance of security reporting
At present, each stakeholder in a business knows about cybersecurity and its job in the business climate. Organization boards are turning out to be more worried about business information privacy and systems security.
The IT division can never again work alone in overseeing security systems, yet everybody, particularly the administration and board, should come in to give support. A cybersecurity report should be quantifiable and give insights concerning the potential dangers that could influence the business targets, upset its procedures, or overpower its risk resilience.
Types of network security
Security threat to organizations is the most terrible kind of danger organizations are managing recently. One of the actions that assist organizations with safeguarding their systems is network security. which assists keep information respectability and convenience in getting across the organization. It recognizes potential threats and keeps them from getting to the network. There are various sorts of network security.
Network access control
In a business with an enormous organization and clients, numerous gadgets can be utilized to get to its network. Without control, unapproved gadgets can be utilized to get to the organization and cause significant threats.
Network access control holds network access under wraps. This organization control distinguishes which gadgets are approved to get to the organization and gives them access while impeding those that are not approved. If somebody with an approved gadget attempts to do a vindictive action, this organization’s control will recognize and hinder them.
Wireless security
Remote working is turning into the standard in each business. Because of this, organizations have made wireless passageways and organizations. Remote access is inclined to assaults and this is where remote security comes in. It guarantees information isn’t hacked while moving it between the fundamental servers to the remote access point and back.
Applications security
Applications today resemble the heart that pushes a business forward. They assist organizations with performing complex undertakings or interface from a distance with their clients. Applications assist clients with getting to their records and exchanges from the solace of their homes. No matter what their significance, they are inclined to assaults. Application security safeguards them.
Email security
Emails are utilized for showcasing and correspondence. They are at higher risk from aggressors who could send misleading emails or divert to malware locales. Email security helps block such dangers or assaults.
Antivirus and hostile to malware security
Viruses assault files and programming, which dials back the system or grounds it. Malware can carry a business system to a stop for quite a long time. The antivirus and anti-malware software helps keep the framework/reports safe.
How would I make a cyber security report?
To begin with, you should grasp three central things
- The sort of information you have
- The framework you have
- The information esteem you need to secure.
Have prepared your cybersecurity report template to assist you with writing the report. You will find definite security report examples online that will assist you with making the structure accurate.
You might ask yourself further inquiries to assist you with auditing your information.
- What various kinds of information does the business gather
- How is this information put away?
- Where is it put away?
- How might the business safeguard its information?
- For how long is the information kept
- How could it be gotten both inside and remotely?
- Assuming the stockpiling secure
- Are there any breaks
- Who is allowed admittance?
You might find more inquiries in your security report test that you can add to your rundown of inquiries. Some security report models may be definite however you need to figure out what will work for your business and adjust it while disregarding what won’t work. Utilizing the cybersecurity report template, start to compose your security report.
How would you write a security report?
You can make your one-of-a-kind security report layout or download a cybersecurity report template on the web. The accompanying data is significant in your security report.
Decide information value
You can have a wide extent of the data you need to give yet it probably won’t be any doubt significant to the business. At the point when the data degree is excessively wide, it could add cost to the business. Organizations work with budgets and you shouldn’t disturb them because of extended reports and proposals.
Pick what is important right now and disregard the rest. Since you are writing a security report, ensure it is secure. Assuming the report is leaked, you will gamble with the organization’s touchy information.
Identify the assets and prioritize them
The business could have a large number of resources that require security. Be that as it may, only one out of every odd resource is important. On the off chance that you play out a risk assessment for every resource, it could require a long investment before your total it. Make a list of what is vital to be accounted for. For instance
- Interfaces
- Applications
- Information
- IT design
- Capacity security
- Equipment security
- Remote access security
- Data stream
Distinguish the digital dangers you have
Cyber threats are the weaknesses the business could have regarding inner assaults, outer dangers, and human blunders. Here is a portion of the significant threats.
Human mistakes: Your labourers or an outsider approaching the framework can cause lethal blunders that can cost the organization misfortunes. On the off chance that they are not knowledgeable on issues of cyber security, somebody can unconsciously open a malware interface that can carry the whole framework to a stop. Recognize the risks that can be brought about by human blunders and alleviation measures.
Data leaks: The security system probably won’t be sufficiently tight, prompting information spills. Significant business information can be found in the public space, which can undermine the respectability of the business.
Unauthorized access: Unauthorized access could be because of password theft, malware assaults, representative inclusion, or programmers.
Normal or man-made disasters: Business information can be compromised by regular or human disasters. Lightning could strike, fire, floods, typhoons, bombings, and so forth. Without appropriate information reinforcement, all organisational information can be lost in one occurrence.
Failed framework: The business framework could fall flat not due to digital goes after yet because of organization associations, equipment challenges, bottleneck issues, and so forth. This is a potential danger that should be accounted for.
Distinguish any weaknesses
After finishing your report on the security dangers that could happen to the business, continue toward the probability of them occurring. Regardless of whether they could occur, the security frameworks can be sufficiently able to keep them from occurring. Nonetheless, even with areas of strength for a framework, there is as yet a likelihood that they can occur.
Your expectation to do is a weakness analysis to test the system and decide how conceivable it is for dangers to work out. You will test the system weaknesses and afterwards make a total report.
What controls are there and the new controls should be implemented
Controls are set up to bypass any chance of threats occurring. In any case, if the controls are feeble and helpless, there ought to be planning to carry out new ones. New controls could be as far as new equipment, a difference in programming, information encryption, new security strategies, better approaches to detect leaks, and so on.
Effect of different situations on a yearly premise
Your next issue will be to distinguish the different situations under which the threats could occur. Right now, you need to go past taking a gander at the probability of a threat occurring and take a gander at its effect on the off chance that it works out.
The inquiries you may be posing to yourself are – could it at any point work out and assuming it works out, how far could the results go? This is the thing that will assist with deciding in your report the worth of speculation your need to alleviate such situations. You should likewise review the worth of the business at present and gauge how that worth would be impacted assuming a threat turned out to be genuine.
List the risks in terms of priorities
A few divisions or frameworks are at a higher gamble if a danger happens. Sort out the amount it would cost the organization to address a gamble on the off chance that it worked out. Assuming remedy estimates cost more than the resource esteem, everything will work out for the best.
Be that as it may, the resource could have a greater effect concerning business reputation. On the off chance that the impact on reputation is greater, it merits spending more to right, regardless of whether its worth is less.
Record the findings
Finish your report by documenting all that and afterwards present it to the administration to understand it. Examine it and suggest. Try not to duplicate data from the security report example you downloaded. Its motivation is to direct you during the investigations and to report.
cfw security incident report template
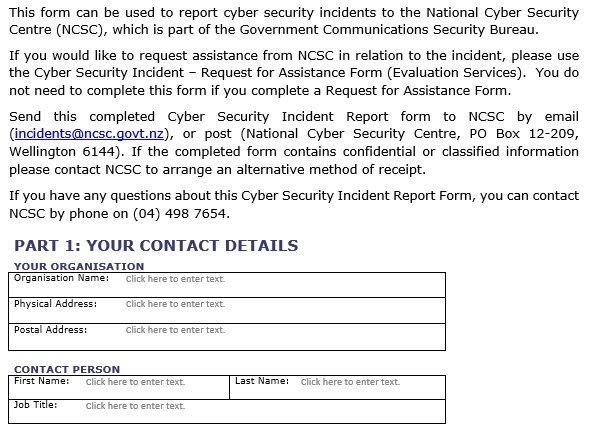
cyber security incident report form
free security report template 3
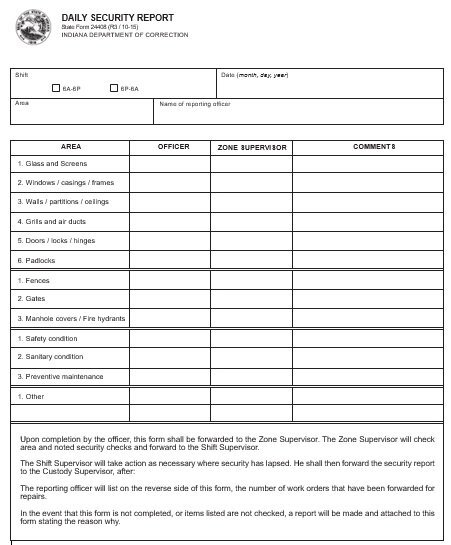
daily security report template
it security audit report template
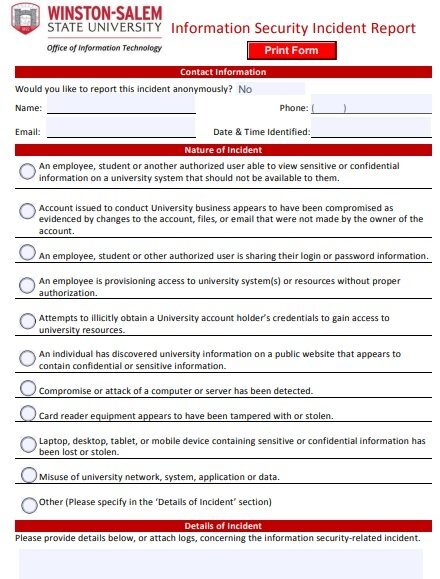
information security incident report template
data security incident response report template
cyber security incident report format
Conclusion
Assuming your business is offering security administration, Security is the free site template that deals with your web-based presence. It has all the required in-store prepared for you to show up as expert as possible. From a major picture pennant, text and source of inspiration button to painstakingly planned about us, administration and group pages, Security have all you want. It likewise includes mind-blowing evaluating tables to illuminate those keen on working with you about the expense and a contact page. The last option has a completely working contact structure and incorporated Google Guides.
A tacky and straightforward menu, online entertainment symbols, pamphlet membership and full responsiveness are other remarkable elements of this free security administration site layout. Deal with everybody’s insurance with Security.



















![25+ Free Punch / Reward Card Templates [Word, PDF] free printable punch card template](https://cdn-ildebcd.nitrocdn.com/jnQCRkBozueuJprueOUxlAYnHGPdsTNY/assets/images/optimized/rev-d7007a4/templatedata.net/wp-content/uploads/2021/05/free-printable-punch-card-template-150x150.jpg)